How Would You Best Describe the Threat Extraction Functionality
This could include anything from other companies who. When using PCA we take as input our original.

Threat Intelligence Framework Documentation Splunk Developer Program
Security and Speed.
. Upon completion of a risk assessment an IS auditor should describe and discuss with management the threats and potential impacts on the assets as well as recommendations for. What percentage of the studies showed a negative effect of organic farming on organisms. Threat detection is the practice of analyzing the entirety of a security ecosystem to identify any malicious activity that could compromise the network.
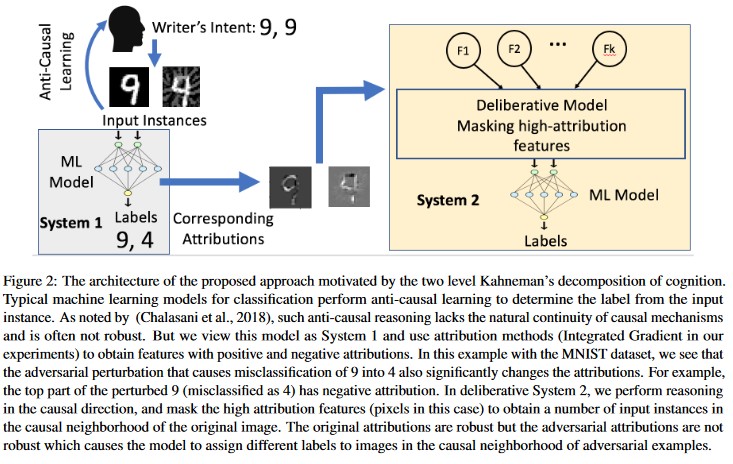
A A new cell wall begins to form. When you hear CIA the first thing you likely think is Central Intelligence Agency which is an independent US. Threat Extraction is a new Software Blade in the Threat Prevention family that pro-actively cleans potential threats from incoming documents.
B The membrane of the nucleus dissolves. As mentioned earlier TTPs describe how and what a threat does. Rather than trying to detect known and unknown malware Threat Extraction.
Ey are abstracted from observed threats to describe the pa erns of malicious activities ie threat actions of a certain. The extraction locates and identifies relevant data then prepares it for processing or transformation. This can be especially beneficial for hazardous waste generators since solvent extraction.
The worlds most abundant fossil fuel. Extraction Part 1 After a reaction is completed the solution often times does not only contain the desired product but also undesired byproducts of the reaction unreacted. Feature Extraction Principle Components Analysis PCA PCA is one of the most used linear dimensionality reduction technique.
Organic extraction methods are considered the gold standard for RNA preparation. During this process the sample is homogenized in a phenol-containing solution and the sample is then. As part of the Check Point SandBlast Zero-Day Protection solution the Threat Emulation engine picks up malware at the.
Reveal Solution Hide Solution Discussion 2. This a new mechanism which extracts malicious files from a document to use it as a counter-attack against its sender. Data is taken from one or more sources or systems.
For which group of organisms is evidence of positive effects the strongest. Government agency that is responsible for. What is the mechanism behind Threat Extraction.
If a threat is detected then mitigation. The Central Intelligence Agency. A mixture of hundreds or thousands of different hydrocarbon molecules.
Primary fuel used in the United States for space and water. Which stage or phase of the cell cycle corresponds to each of the descriptions below. A chemical that will dissolve another chemical in a liquid extraction the third chemical that is added to extract the solute.
Try These 5 Steps to Complete a Successful Threat Assessment. Feature extraction is a part of the dimensionality reduction process in which an initial set of the raw data is divided and reduced to more manageable groups. In business analysis Threats are anything that could cause damage to your organization venture or product.
Solvent extraction is used to separate hazardous contaminants from sludge and sediments as well. C Each instance of VRRP running on a supported interface may monitor the link state of other interfaces. Collect Necessary Data to Cover the Full Scope of Your.
Describe two advantages of extraction systems. Determine the Scope of Your Threat Assessment. Preventing todays sophisticated attacks requires innovation.
Threat Extraction provides preemptive and proactive protection.
![]()
Zero Day Protection Check Point Software

Advanced Network Threat Prevention Check Point Software
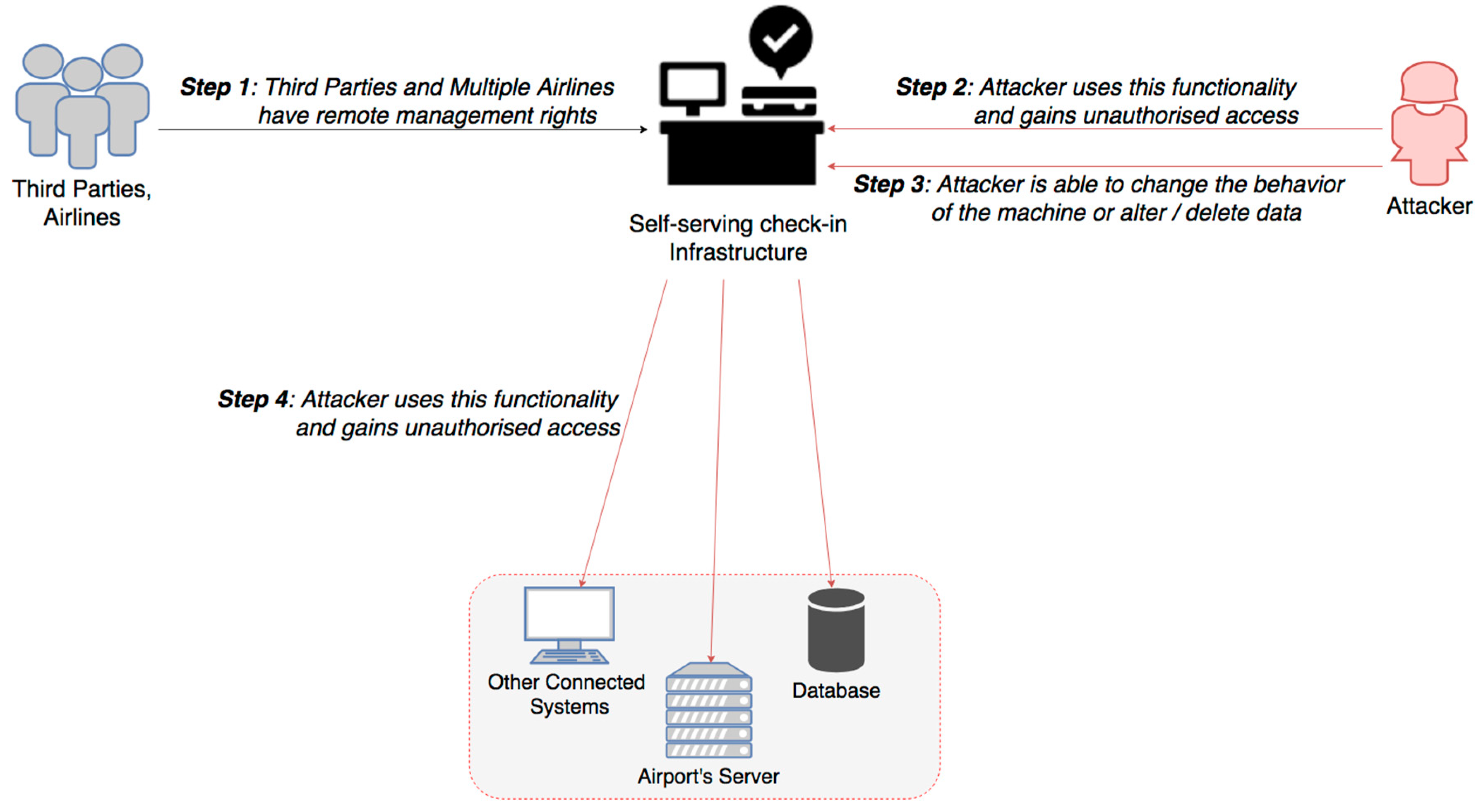
Sensors Free Full Text Smart Airport Cybersecurity Threat Mitigation And Cyber Resilience Controls Html

Threat Modeling Ai Ml Systems And Dependencies Security Documentation Microsoft Docs
No comments for "How Would You Best Describe the Threat Extraction Functionality"
Post a Comment